When managing a VPS server, ensuring its security should be a top priority. Below are two important steps you should take to help protect your server from potential attacks:
1. Change the Default SSH Port
SSH runs by default on port 22, making it a common target for attackers. By changing the SSH port to a non-default port, you can make it harder for attackers to find and exploit it.
Steps to Change the SSH Port:
- Edit the SSH Configuration File:
- Open the SSH configuration file with a text editor (e.g.,
nanoorvi):
- Open the SSH configuration file with a text editor (e.g.,
sudo nano /etc/ssh/sshd_config
- Change the Port Number:
- Find the line that says
#Port 22, and change it to your desired port number (for example,Port 2222):
- Find the line that says
Port 2222
- Save the Changes:
- Save the file and exit the editor (for nano, press
CTRL+O, thenCTRL+X).
- Save the file and exit the editor (for nano, press
- Restart the SSH Service:
- Restart the SSH service to apply the changes:
sudo systemctl restart sshd
- Update Firewall Settings:
- Ensure that your firewall allows access to the new SSH port. If you are using
ufw(Uncomplicated Firewall), allow the new port (e.g., port 2222):
- Ensure that your firewall allows access to the new SSH port. If you are using
sudo ufw allow 2222/tcp
- If necessary, block the default SSH port:
sudo ufw deny 22/tcp
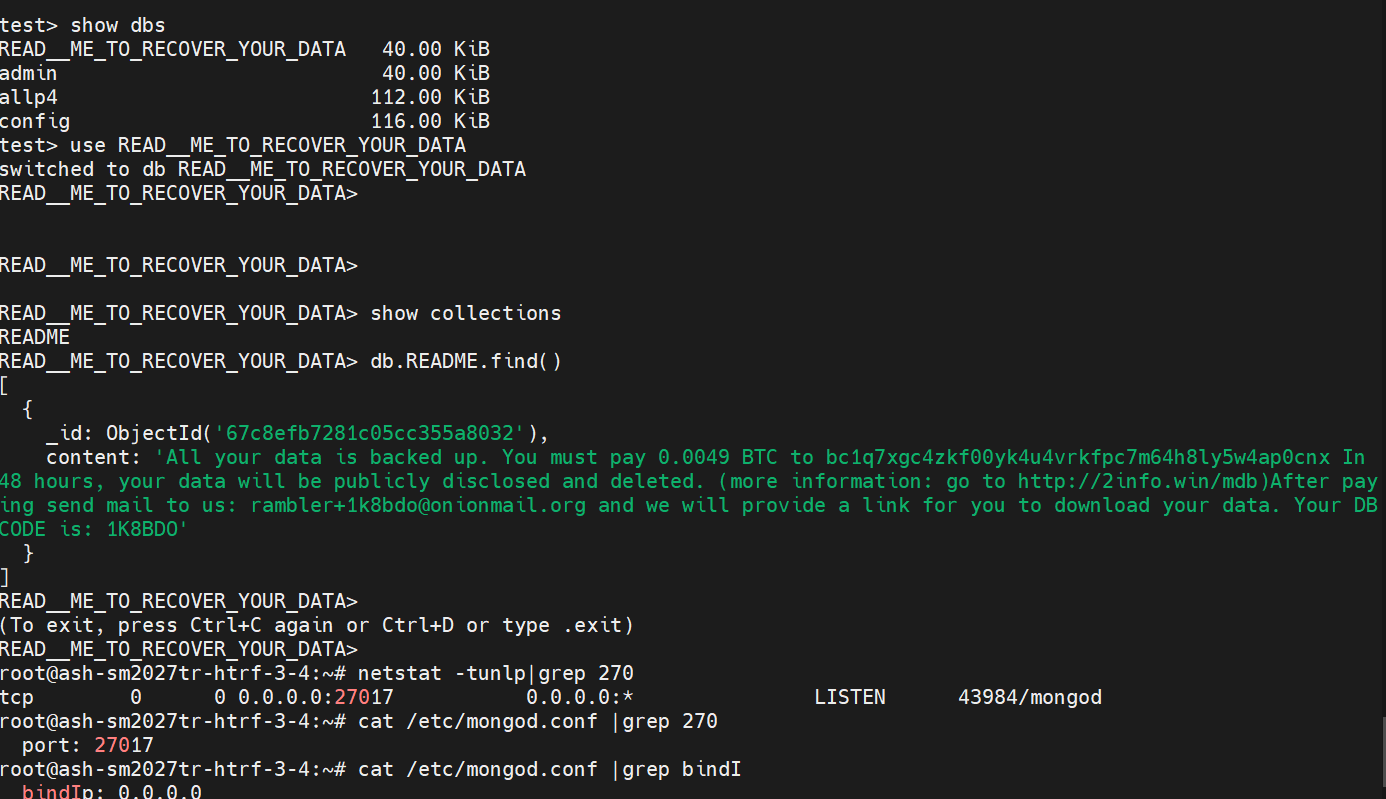
- Disable MongoDB Access from 0.0.0.0 By default, MongoDB is bound to
0.0.0.0, meaning it can be accessed from any IP address. This poses a serious security risk as it exposes your MongoDB database to potential attackers on the public internet.
Steps to Disable MongoDB Access from 0.0.0.0:
- Edit the MongoDB Configuration File:
- Open the MongoDB configuration file in a text editor:
sudo nano /etc/mongod.conf
- Change the Bind IP Address:
- Find the
bindIpoption under thenetsection. By default, it may be set to0.0.0.0(allowing access from any IP address). Change it to127.0.0.1(allowing access only from the local server) or another trusted IP address:
- Find the
net:
bindIp: 127.0.0.1
- Save the Changes:
- Save the file and exit the editor (for nano, press
CTRL+O, thenCTRL+X).
- Save the file and exit the editor (for nano, press
- Restart MongoDB:
- Restart MongoDB to apply the changes:
sudo systemctl restart mongod
Final Steps:
After completing these changes, your server will have significantly improved security:
- SSH will no longer be accessible on the default port 22.
-
MongoDB will only be accessible locally, reducing the risk of remote attacks.
By following these simple steps, you enhance your server’s defense against unauthorized access. Always remember to regularly check your configurations and monitor your server for suspicious activity. Stay safe!