From: https://restoreprivacy.com/webrtc-leaks/
When discussing online privacy and VPNs, the topic of WebRTC leaks and vulnerabilities frequently comes up.
While the WebRTC issue is often discussed with VPN services, this is, in fact, a vulnerability with web browsers. WebRTC leaks can affect these browsers: Chrome, Firefox, Safari, Opera, Brave, and Chromium-based browsers.
So what is WebRTC?
WebRTC stands for “Web Real-Time Communication”. This basically allows for voice, video chat, and P2P sharing within the browser (real-time communication) without adding extra browser extensions.
What is a WebRTC leak?
A WebRTC leak is when your external (public) IP address is exposed via your browser’s WebRTC functionality. This leak can de-anonymize you via WebRTC APIs, even if your VPN is working correctly.
If you have not protected yourself against WebRTC leaks in your browser, any website you visit could obtain your real (ISP-assigned) IP address through WebRTC STUN requests. This is a serious problem.
While the WebRTC feature may be useful for some users, it poses a threat to those using a VPN and seeking to maintain their online privacy without their IP address being exposed.
How to test for WebRTC leaks
Our guide on testing your VPN lists a few different WebRTC testing tools:
- ipleak.net – In addition to WebRTC leaks, this website also tests for IPv4, IPv6, and DNS leaks.
- BrowserLeaks WebRTC test
- Perfect Privacy WebRTC test
What does a WebRTC leak look like?
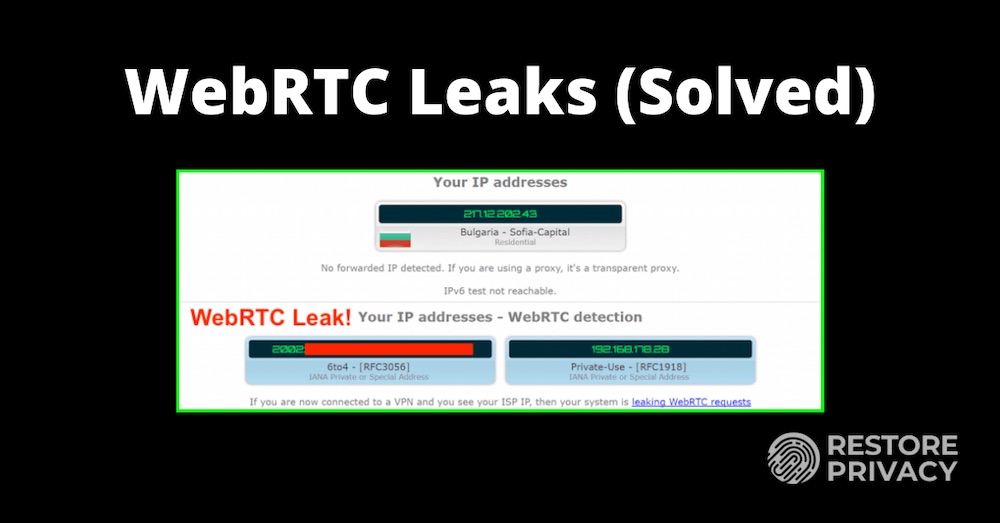
If you see your ISP-assigned (external) IP address, then this is a WebRTC leak. Below is an example of WebRTC leaks that I found when testing out a VPN service. You can see that my public IPv6 address (beginning with 2) is leaking in the WebRTC area, even while the VPN is connected and stable.
Note that a local IP address is blacked out on the left. These cannot be used to identify you. (An explanation of the difference between your local/internal IP and your public/external IP is here.)
The WebRTC Vulnerability
Anyone seeking to be anonymous online through privacy technology should take action against WebRTC leaks.
Daniel Roesler exposed this vulnerability in 2015 on his GitHub page, where he stated:
Firefox and Chrome have implemented WebRTC that allow requests to STUN servers be made that will return the local and public IP addresses for the user. These request results are available to javascript, so you can now obtain a users local and public IP addresses in javascript.
Additionally, these STUN requests are made outside of the normal XMLHttpRequest procedure, so they are not visible in the developer console or able to be blocked by plugins such as AdBlockPlus or Ghostery. This makes these types of requests available for online tracking if an advertiser sets up a STUN server with a wildcard domain.
Essentially, this means that any site could simply execute a few Javascript commands to obtain your real IP address through your web browser.
WebRTC leak solutions
Here are two options for dealing with the WebRTC issue:
1. Disable WebRTC in the browser (Firefox) and only use browsers with disabled WebRTC capability. (Instructions are below.)
2. Use browser add-ons or extensions if disabling WebRTC is not possible. (Disabling WebRTC is not possible with Chrome and Chromium-based browsers, such as the Brave browser.)
Note: browser add-ons and extensions may not be 100% effective. Even with add-ons, the vulnerability still exists in the browser to reveal your true IP address with the right STUN code.
WebRTC fixes for different browsers
Below are different fixes for various browsers.
Firefox browsers
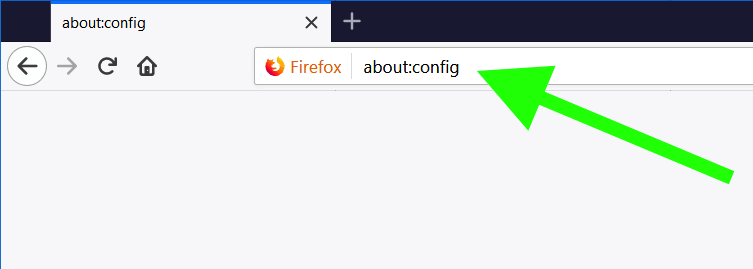
Disabling WebRTC is very simple in Firefox. First, type about:config into the URL bar and hit enter. Then, agree to the warning message and click the continue button.
Then, in the search box type “media.peerconnection.enabled“. Double click the preference name to change the value to “false“.
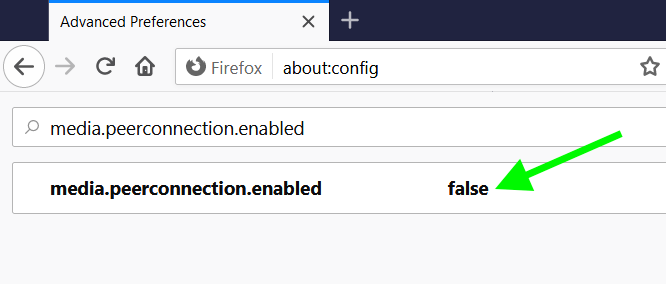
That’s it.
WebRTC is now disabled in Firefox and you won’t have to worry about WebRTC leaks.
Chrome WebRTC (desktop)
Since WebRTC cannot be disabled in Chrome (desktop), add-ons are the only option (for those who do not want to just give up on using Chrome).
As pointed out above, it is important to remember that browser add-ons are may not be 100% effective. In other words, you may still be vulnerable to WebRTC IP address leaks under certain circumstances. Nonetheless, here are some add-ons that may be worth considering:
Note: Unlike with Firefox, these extensions only change WebRTC’s security and privacy settings.
Recommended solution: stop using Chrome.
Disable Chrome WebRTC on Android
On your Android device, open the URL chrome://flags/#disable-webrtc in Chrome.
Scroll down and find “WebRTC STUN origin header” – then disable it. For safe measure, you can also disable the WebRTC Hardware Video Encoding/Decoding options, though it may not be necessary.
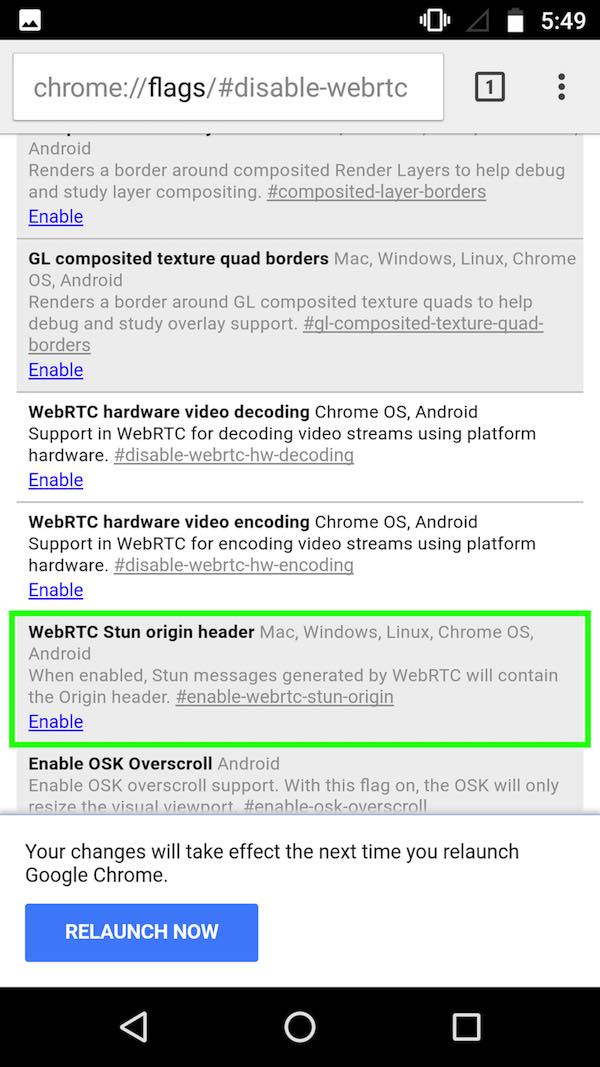
Note: Android users can also install Firefox, and disable WebRTC via the steps above.
Chrome iOS WebRTC
Chrome on iOS does not appear to implement the vulnerable parts of WebRTC that could expose local or external IP addresses (yet).
Brave WebRTC leaks
Because the Brave browser is based on Chromium, it is also vulnerable to WebRTC IP address leaks, even when you are using a VPN.
There are two ways to block WebRTC in the Brave browser:
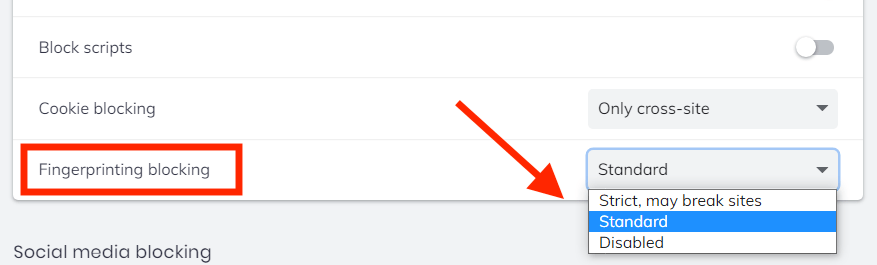
Method 1: Fingerprinting protection
Go to Settings > Shields > Fingerprinting blocking > and then select Standard or Strict. This should take care of all WebRTC issues – at least on desktop versions of Brave (Windows, Mac OS, and Linux).
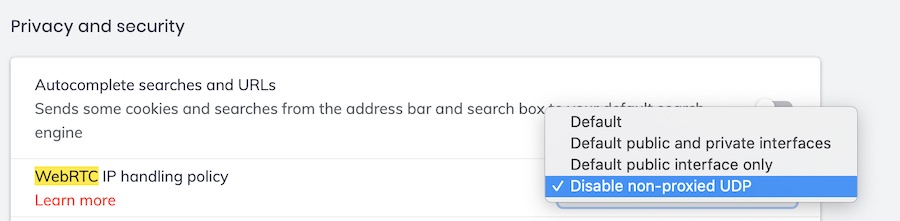
Note on WebRTC handling policy
You can also adjust the WebRTC handling policy if you go to Settings, click on the search glass in the upper-right corner, and then enter WebRTC. Under the WebRTC IP Handling Policy click the drop down menu and you can see the options below.
Note: To understand the different options with WebRTC handling, Brave has an article on the topic here. Below are the different options:
I have now tested this with the latest versions of Brave for Windows and Mac OS. Based on my tests, if you already have Fingerprinting blocking set to enabled, you should not experience any WebRTC leaks.
Note: I have seen some complaints from users who claim that WebRTC is not getting blocked on iOS, even after making the changes above. Brave developers appear to have confirmed this issue and are working on a fix.
Safari WebRTC
WebRTC leaks have traditionally not been an issue with Safari browsers (on Mac OS and iOS devices). However, Apple is now incorporating WebRTC into Safari, although it’s still technically an “experimental” feature. Nonetheless, it’d be wise to disable WebRTC in Safari for privacy reasons. Here’s how:
- Click “Safari” in the menu bar
- Then click Preferences
- Click on the “Advanced” tab, then at the bottom check the box for “Show Develop menu in menu bar”
- Now, click on “Develop” in the menu bar. Under the “WebRTC” option, if “Enable Legacy WebRTC API” is checked, click on it to disable this option (no check mark).
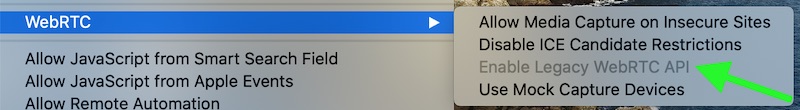
That should effectively disable WebRTC in Safari.
Opera and other Chromium browsers WebRTC
Just like with Chrome, the only way (as of now) to address the WebRTC vulnerability in Opera and other Chromium browsers is to use an extension.
First, download the extension “WebRTC Leak Prevent” to your Opera browser.
Then in the Advanced options for the WebRTC Leak Prevent extension, select “Disable non-proxied UDP (force proxy)” and then click Apply settings.
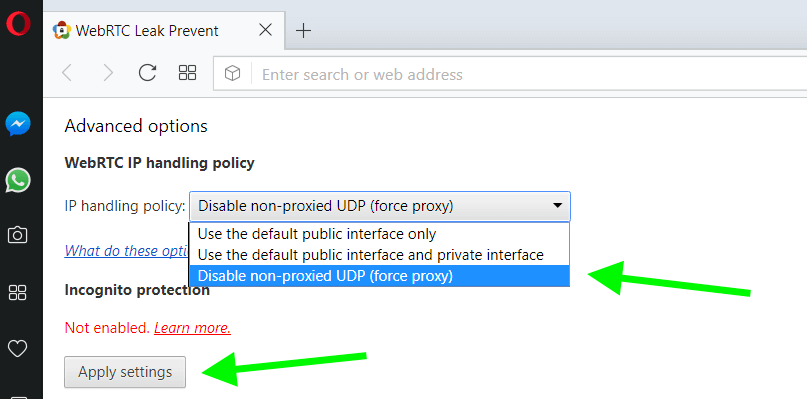
Again, because this is an extension solution, it may not be 100% effective.
Now verify you don’t have any WebRTC leaks
Now that you have disabled or blocked WebRTC in your browser, you should test to verify that it is working. Here are our favorite tools for identifying WebRTC leaks:
Note: If you are seeing a local IP address, this is not a leak. A WebRTC leak will only be with a public IP address.
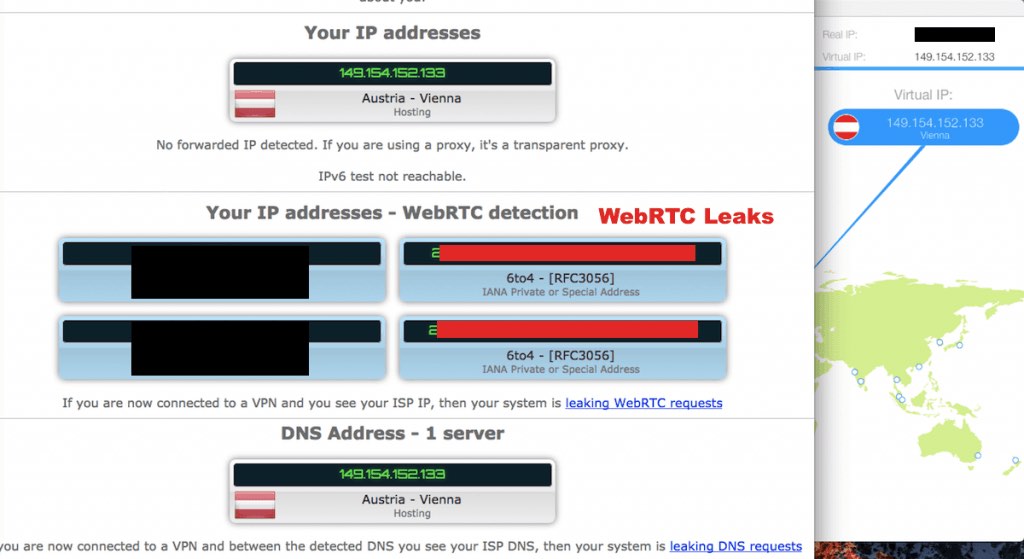
Here I’m running a test in the Firefox browser while also connected to ExpressVPN:
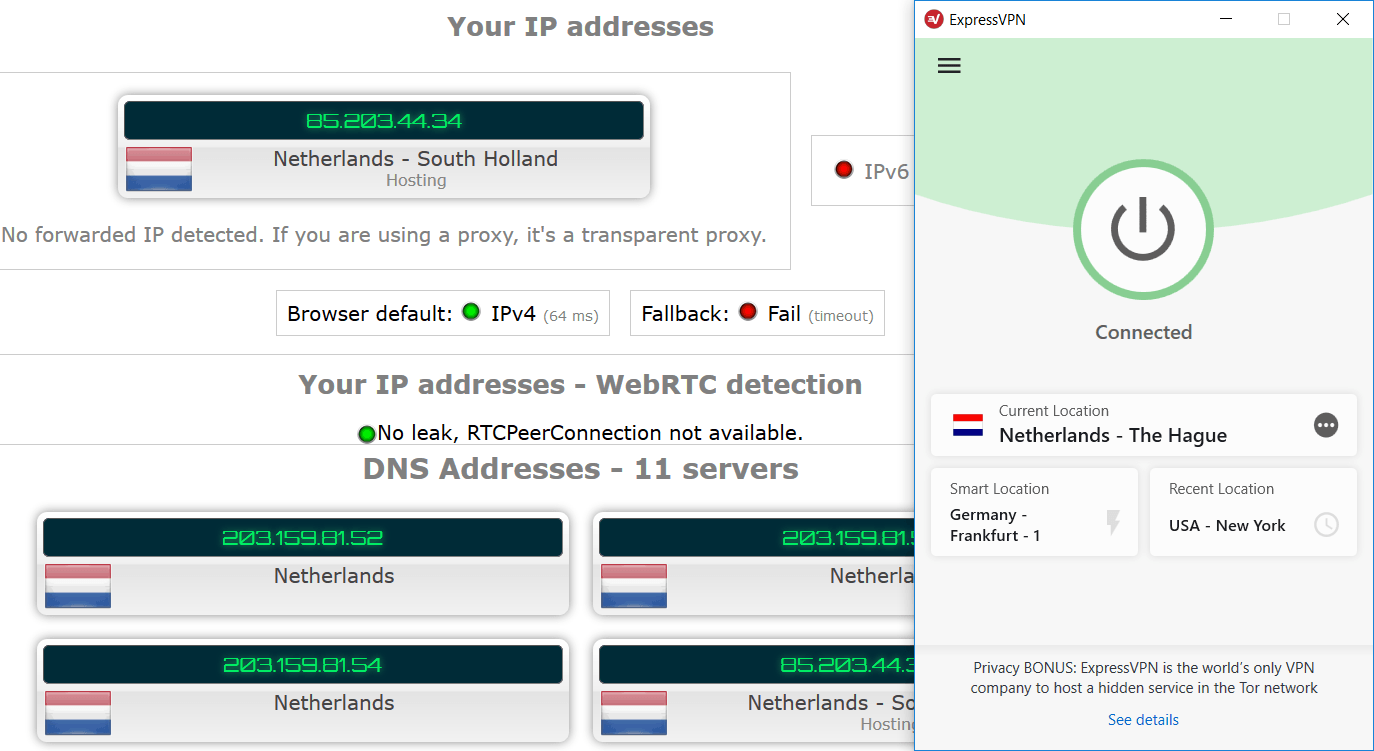
You can see the ExpressVPN client on the right, with the test results on the left. No leaks!
Note: ExpressVPN is currently our top VPN recommendation and they also have a discount for three months free, see our ExpressVPN coupon page for details.
Conclusion on WebRTC leaks and browser vulnerabilities
The WebRTC leak vulnerability highlights a very important concept for those seeking a higher level of online anonymity and security through various privacy tools.
The browser is usually the weak link in the chain.
The WebRTC issue also shows us that there may be other vulnerabilities that exist with your privacy setup, even if you are using a good VPN to hide your IP address and location. (The WebRTC issue was not publicly known until 2015.)
One other problem to be aware of is browser fingerprinting. This is when various settings and values within your browser and operating system can be used to create a unique fingerprint, and thereby track and identify users. Fortunately, there are effective solutions for this as well.
And lastly, there are many different secure and private browsers to consider, many of which can be customized for your own unique needs.
Stay safe!